Contents
In this article I’ve provided a script which can be used to replace the default SSL certificate on your VCSA with a new signed certificate by your enterprise certificate authority.
Further, you can also use this same script to replace your signed certificate, prior to it expiring.
Background
The manual process to replace your VCSA SSL certificate is simplified in recent versions of the VCSA, however this is still a manual process which should be completed at least every year. If you’re interested in my article on how to manually replace your VCSA Web SSL Certificate, check here: How to manually sign your vCenter Server SSL Certificate
If you have environments with many vCenter Servers it is not ideal to complete this process manually, this is especially true when you end up having to replace multiple certificates at the same time, before a deadline.
Manual installation of signed SSL certificates is also a top reason why often those responsible for the organization’s VCSAs neglect to install a signed SSL certificate in the first instance – It is just too much work to manage on top of already increasing workloads.
The script to replace your vCenter Server Web SSL Certificate
Using PowerShell, the vCenter REST APIs and Microsoft’s certreq tool, we can manage the complete lifecycle of VCSA Web SSL certificates!
The script performs the following steps:
- Creates a Certificate Signing Request (CSR) on the VCSA (Leaving the private key on the system for best security practices)
- Downloads the CSR
- Sends the CSR to your Microsoft Certificate Authority for signing, with a given CA Template
- Downloads the signed certificate
- Uploads the certificate and certificate chain to the VCSA
- Restarts the VCSA services to make the new certificate take effect
What do you need to use the script?
Permissions
- You will need to run the PowerShell script with an account that is able to sign certificates with your Microsoft Certificate Authority.
CA Template
- The Microsoft Certificate Authority comes with a default “WebServer” Signing Template. You should clone, enable and adjust the configuration based on your preferences.
- Ensure the user you run the script as, has permission to sign against this template. More info.
Certificate Chain
- The script does not currently create the certificate chain by itself. You’ll need to obtain this yourself from your CA.
Certreq
- The script uses the certreq executable, this is available on most Windows operating systems, so be sure to run your PowerShell script on one with certreq available and in the PATH environment variable. To validate this, open a PowerShell window and type
certreq -?to see if the application responds with the help information.
Other
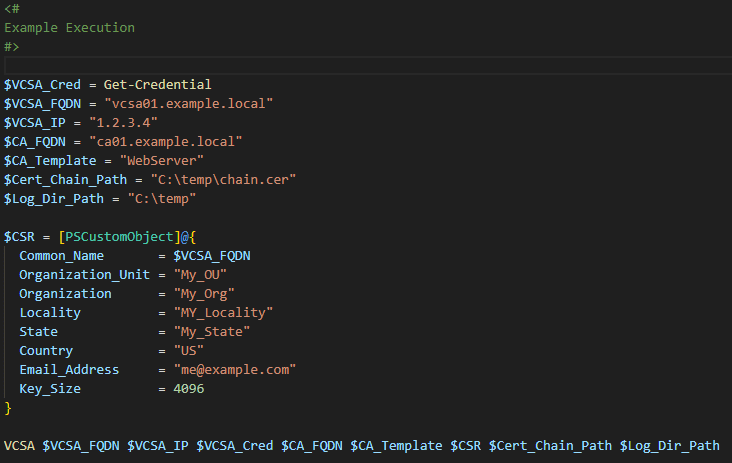
- Naturally you will also need credentials for your VCSA with permission to mange certificates and a few other details for the CSR. You can find all the configurable variables in the example.
How do I use the script?
At the bottom of the VCSA.ps1 script there are a number of variables to populate. Set these variables then execute the script.
Where do I download the script?
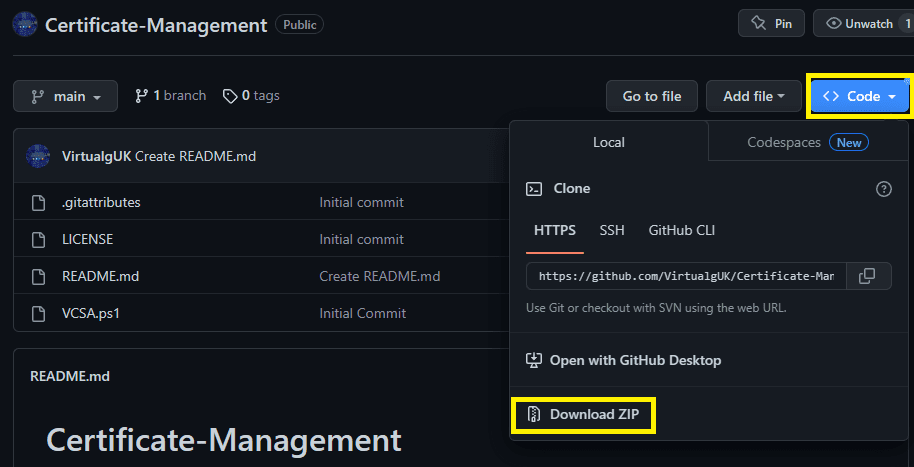
The script is located over on GitHub: VirtualgUK/Certificate-Management (github.com)
To download a copy of the script select <> Code then Download Zip
Feedback
This script is still under development and as such may not work as required, I cannot accept any liability for this. Please do your own due-diligence.
If you find any bugs, have any feature/integration requests or other feedback, please let me know via Twitter / E-mail or via GitHub